Using OCR for identifying RMF Boundary Diagrams - Python
Page under construction…
NAVY RMF
The Navy Risk Management Framework (RMF) is a structured approach aimed at managing cybersecurity risks within information systems. The process encompasses system identification, categorization based on impact levels, and the selection and implementation of security controls. Through rigorous assessments, the effectiveness of these controls is evaluated, leading to authorization decisions by an Authorizing Official (AO). Continuous monitoring and documentation are integral parts of the process, ensuring that information systems not only meet security standards but also adapt to evolving threats.
The RMF process emphasizes a commitment to ongoing risk management, periodic assessments, and continuous improvement throughout the lifecycle of information systems. By addressing emerging vulnerabilities and staying aligned with evolving security requirements, the Navy aims to maintain a robust cybersecurity posture in its information systems.
Boundary/Topology Diagram
The Navy Risk Management Framework (RMF) process, when incorporating boundary diagrams, involves several key steps. Initially, a boundary diagram is created to define the scope and context of the information system. The process starts with system preparation, where the system and its purpose are identified, and the boundary diagram helps establish clear system boundaries.Throughout the Navy RMF process, the boundary diagram serves as a visual aid to ensure a clear understanding of the information system’s components, relationships, and interactions. This visual representation contributes to effective risk management and compliance with security standards.
The boundary diagram adheres to a specific standard and is consistently cross-referenced with an asset list. I won’t delve into the detailed requirements of the boundary diagram but I will aim to simplify it. This project, functioning as a proof of concept, may seem overly excessive in its application. Nevertheless, it serves as a venture driven by my curiosity and a commitment to refining my skills in Machine Learning.
Most requirements follow the DISN CPG, section E.5.
General Steps
- Create a simplified Topology Diagram
- Create an asset
- Apply OCR in the Topology Diagram
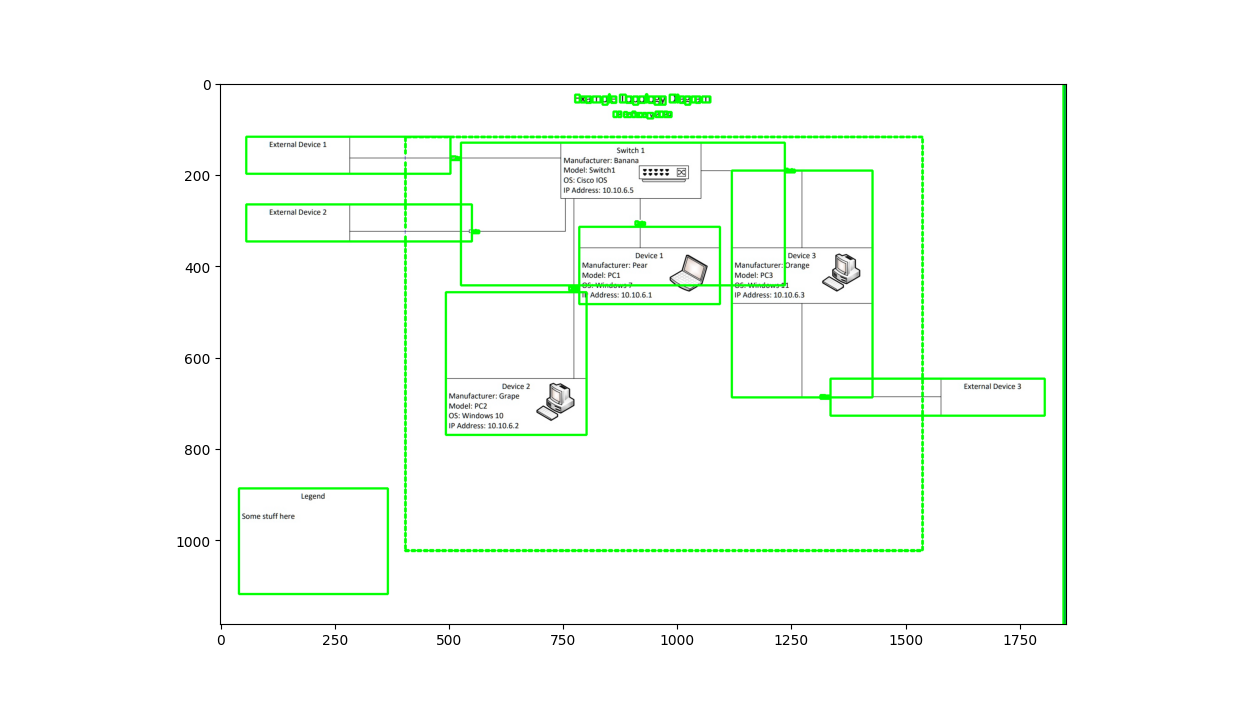
Topology Diagram
In this section, I created a sample topology diagram following some requirements in the DISN CPG. In the diagram below, we have 3 external devices, and 4 devices withinn the delineated authorization boundary marked in red. Note that within the boundary, Device names, Manufacturer, Model, OS, and IP Address are clearly expressed.
Applying OpenCV in the Topology Diagram
I aim to divide the diagram into two parts. A snapshot of the devices outside the boundary and another for the device inside the delineated boundary. This will remove the excess raw data of the devices outside the boundary.
I will be using OpenCV to determine the edges, however, there are some obstacles along the way.
1) I want the program to be general use, hence, not only should it work for my diagram but also others. 2) Since data flow between boxes (devices) exist, OpenCV will sometimes commit to thinking that it is an edge/contour boundary. 3) Not all boxes are captured or too much are captured.
Below is an example of case (3). In the image below, while not properly using the right parameters, it is easy to capture every possible means openCV captures a “rectangle”. Hence, it is essential to find a way to either use multiple imaging processes and/or use better parameters.
After some experimentation, I was able to get the following results:
 .
.
Now the next step is to crop the following image mask and inject it to pdf miner.
A Simple Method
Since the network topology diagram is (usually) created digitally, then tools such as pdfminer or pdfminer.six allows for an easy method to mine text in the pdf file. For example, simply executing commands:
from pdfminer.high_level import extract_text
text = extract_text("example.pdf")
print(text)\
would give us the all text within the document. However, since we already excluded the boundary, we will only be getting the devices inside using pdfminer. Another case of this project, would be to use another form of edge detection inside the boundary to get all the inside squares. However, I came to realize that in the RMF world, labels and description of the devices aren’t necessarily organize inside the boundary.
Future Development
As stated above, using another edge detection would be ideal for this project. However, due to time interest in another project, I will be moving on. There are a cases to improve in this project:
- Create an Asset List (csv) using the mined text.
- Compare it to an already existing Asset List for validation.
